Genexis Platinum-4410 Wireless Router Authentication Bypass Vulnerability (CVE-2020-6170)
This Story is about How I exploited a widely used Fiber Router in Europe & India
The Genexis Platinum-4410 Wireless Router Authentication Bypass Vulnerability is the one I found when I was was simply browsing the router pages.
Device Model:Platinum-4410
Hardware Version: V2.1
Software Version: P4410-V2–1.28
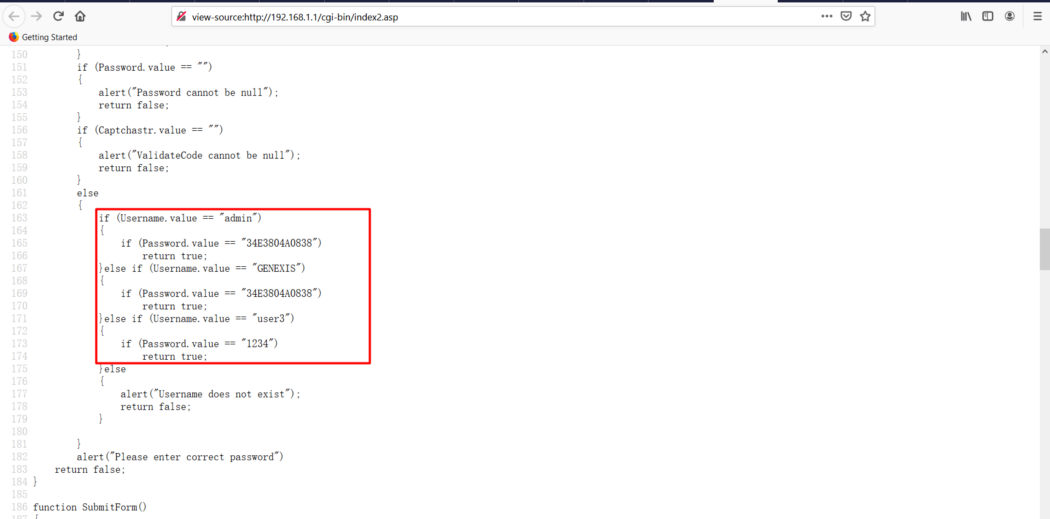
while checking the source code of login page “http://192.168.1.1/cgi-bin/index2.asp”, I found the passwords of each login accounts in clear text! Clearly it is a critical vulnerability in Genexis Router
First we need the router IP, which is usually IPV4 Default Gateway IP. We can find this using ipconfig /all command from cmd or checking details of network adapter connected to network from Network and Sharing Center.
Most common default router IPs are 192.168.0.1, 192.168.1.1 etc. Go to the router IP 192.168.1.1, it will automatically shows the login page “http://192.168.1.1/cgi-bin/index2.asp”. Check view page source, here we can found passwords of each login accounts in clear text.
- Vulnerability reported to Genexis team.
- Team confirmed and fixed on latest firmware
-
Awarded CVE-2020-6170
- References:
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-6170
- https://medium.com/@husinulzsanub/exploiting-router-authentication-through-web-interface-68660c708206
made with ☕ and 🛠️
